1. Initial Incident
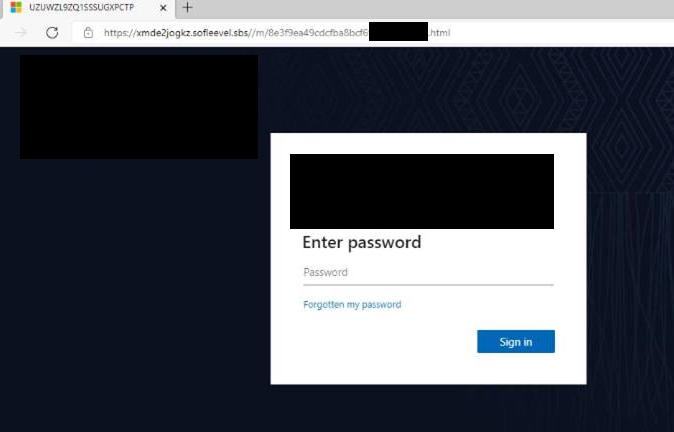
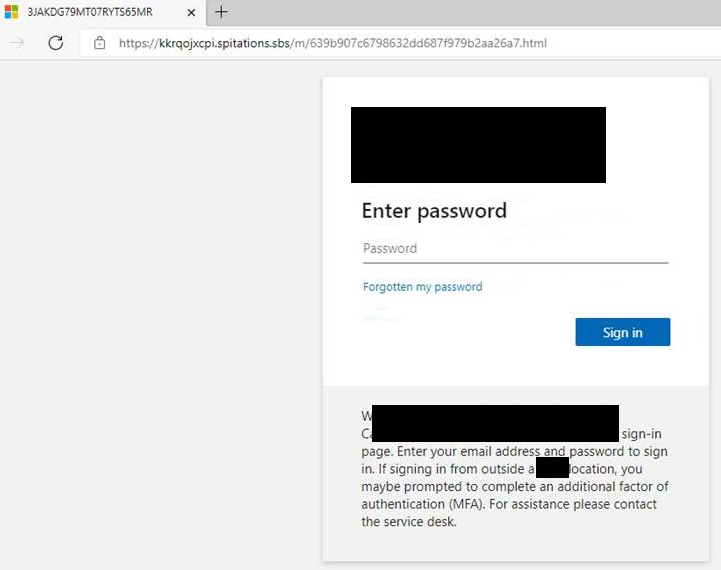
Late 2023, we observed several of our users , working in different locations with different email domains but all either executive assistants or members of the different finance teams, receiving suspicious emails that ultimately directed users to fake Microsoft 365credential harvesting pages. All the different domains/locations had different 365 login page templates and these were replicated by the actor.
1.1 Indicators
Initial Email URL IOC:
- hxxp[://]bmwag-rt-prod2-t[.]campaign[.]adobe[.]com/r/?id=h2ccc12b,8d23fb3,492093b&p1=//abigfathen[.]com/[.]kasi//[base64 encoded username/snip]
Compromised Website URL IOCs:
- hackervideo[.]com
- thomasrichardengineeringnode[.]com
- abigfathen[.]com
365 Harvesting Page Website IOCs:
- xmde2jogkz.sofleevel[.]sbs
- jhue92s57pdym1k.xngyuqdfkb[.]ru
- kkrqojxcpi.spitations[.]sbs
- dqtrf7hmcu.mouthan[.]sbs
The actor utilised a url redirect flaw for an adobe.com service to bypass standard email security filtering. This initial adobe redirect url would send the user to one of 3 compromised 3rd party websites which were part of a phishing as a service infrastructure. This compromised website would base64 decrypt the recipients email and direct them to the relevant 365 templated harvesting page.
Looking at the compromised/exploited websites in the wayback archive showed these sites to be all based on differing technologies and to have low maintenance/poor security hygiene so were obvious candidates to be exploited.
1.2 WSO Webshell
Checking the compromised websites led us to find a WSO webshell still active.
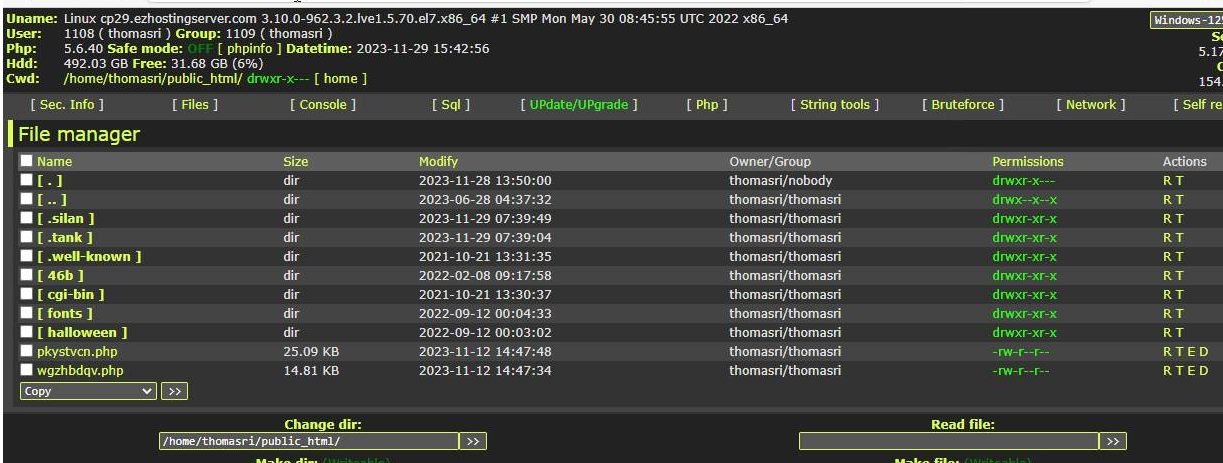
With a bit of trial and error we were able to get the apache logs off the compromised website to try and ascertain extra information about who was targeted alongside our specific users.
This showed actors coming from IP addresses relating to ISPs such as
- hostroyle
- ovh.com
- leaseweb.com
- datacamp.co.uk
- unus.com
- strongvpn.vom
- keminet.com
- digitalocean.com
initiating different phishing campaigns targetting different companies and user bases (albeit Financial companies featured regularly). One company targetted was rothschildandco.com, a large european finance company which had over 220 users contact the compromised host which is likely Rothschilds email filtering solution and not a company full of users with very poor security awareness.