We have recently identified a persistent credential stuffing attack against some of our customers.
Credential stuffing is a cyberattack method in which attackers use lists of compromised user credentials to breach into a system. The attack uses bots for automation and scale and is based on the assumption that many users reuse usernames and passwords across multiple services
When i say some of our customers, I am talking about half of them in our healthcare portfolio. Checking across other industry portfolios doesn’t seem to show any signs. While this isnt smoking gun, based on the length of time and volume, I would have expected some of the other industry customers to have signs.
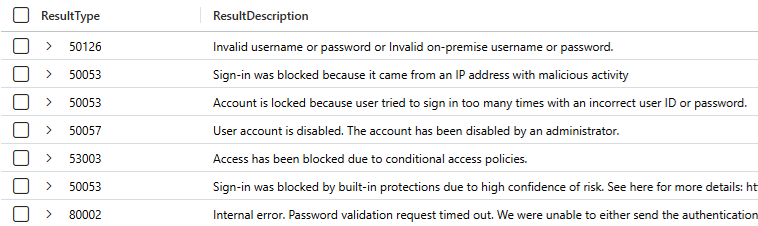
There are several IOCs in common for every attempt stretching back over a year, and these show in the EntraID SigninLogs table as:
- AppDisplayName: Azure Portal
- DeviceDetail: {“deviceId”:””,”operatingSystem”:”Windows10″,”browser”:”Firefox 105.0″}
- UserAgent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0
The logins originate from thousands of different IP addresses across 80+ countries so this rules out using location as a way to identify the actor.
From spot checks we have carried out, the user accounts attempted appear to have been on compromised credential lists, many for sale on the dark-web as a result of infostealers and the date the credentials were taking range from 20 months earlier to within the past fortnight.
Have any of you seen any signs of login attempts using the IOCs above? If you have what industry does it relate to?