Posted inMalware Threat Intelligence
Credential Stealer Malware Trends 2023
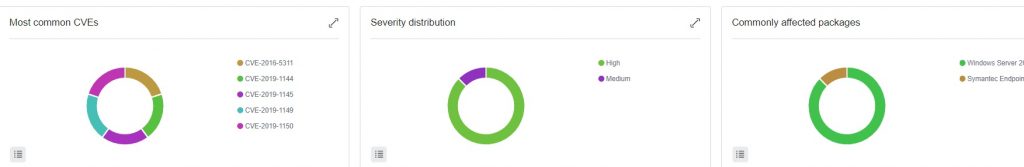
The usual credential stealing malware have consistently booked the top 4 spots each quarter of 2023, albeit jostling amongst themselves for the top position. Meta stealer has shown a constant…