Microsoft have an API to add IOCs to the threat intelligence module in sentinel which can you read about here. My issue with it, is that is is full of bugs or unknown voodoo magic.
Take the DELETE API for example. Say you have an IOC in the Threat intelligence module you need to delete, maybe urgently because it is a false positive IOC causing incidents to be falsely generated. An API exists which is great but trying to make sense of it is crazy. First of all you need the name of the IOC (which is a unique UUID). So before deleting via the API you need to do a query to find the IOC and find and extract the name UUID from the results.
Not you have the name, you can try deleting it. The API looks straight forward, you run it and get a 200 response back. All good..right?
DELETE https://management.azure.com/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/ Microsoft.OperationalInsights/workspaces/{workspaceName}/providers/Microsoft.SecurityInsights/threatIntelligence/main/indicators/{name}?api-version=2023-11-01
If you run the Threat Intelligence query API again the IOC no longer returns as a valid IOC. So it is all good then….right?
This is where it gets interesting. The IOC will have disappeared from the Microsoft Sentinel Threat Intelligence UI , however in the underlying ThreatIntelligenceIndicator table the IOC remains without any changes to the data. This is where the problem comes in as you write your analytics based on joining the ThreatIntelligenceIndicator log analytics table to your other Sentinel tables to create incidents. So the fact Microsoft have made their DELETE API remove IOCs from the UI and API doesnt stop them from generating alerts.
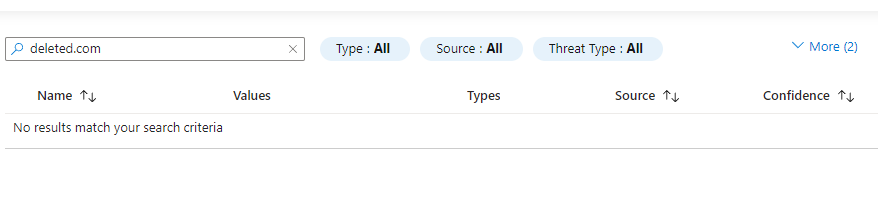
To get around this I use the CREATE API instead of the DELETE API and update the revoked status of the IOC to equal false.
PUT https://management.azure.com/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/ Microsoft.OperationalInsights/workspaces/{workspaceName}/providers/Microsoft.SecurityInsights/threatIntelligence/main/indicators/{name}?api-version=2023-11-01
This creates a new row in the ThreatIntelligenceIndicator table, with the active field set to false which you can have your analytics respect this setting and not have incidents be created.
Here hoping Microsoft fix some of these bugs and start documenting their voodoo a bit better in the near future.
Update December 2024
Microsoft you have done it again! Now the buggy API is not respecting the revoked status properly. So now I am resorting to re-adding the IOC with an expiry time for 10 minute in the future. I shall never be defeated by your APIs Microsoft!